Cyber risk
What do we mean by cyber risk?
Cyber risk refers to any risk of financial loss, disruption or damage to the reputation of an organisation that arises from the failure of its information technology systems.
High risk, high priority
A global survey of audit committee chairs carried out by KPMG in 2015 has highlighted cyber security, including data privacy and protection of intellectual property, as a major concern. This is no surprise given the number of media reports revealing how criminals are exploiting the convenience and anonymity of the internet to commit a diverse range of activities that know no bounds.
In his first speech on cyber crime in May 2009, President Obama highlighted the reliance we place on modern technology and summarised the key threats as 'the disgruntled employee on the inside, the lone hacker a thousand miles away, organised crime, the industrial spy and, increasingly, foreign intelligence services'. He went on to say that, 'it's been estimated that last year alone cyber criminals stole intellectual property from businesses worldwide worth up to $1 trillion.'
A roundtable meeting of European chief audit executives in May 2015 also highlighted the main types of cyber threat and target sectors:
1. Theft of personal data
What?
Customers' or employees' personal data, payment data, insurance data.
Why?
To sell them to ad agencies (up to 3€ per record) or to criminal organisations (20€ to 40€ per credit card).
Who?
Large organisations, with an increased risk in retail, telecoms, banking, insurance, water and utilities, transportations sectors.
2. Divulgence of sensitive information
What?
List of 'forbidden' or 'unethical' customers, suppliers, transactions, payments.
Why?
To damage the company’s reputation.
To foster a more ethical behaviour.
Who?
Financial services: banks, insurance companies.
Companies active in countries at risk include mining, oil exploration and defence.
3. Theft of classified data
What?
Industrial knowledge, commercial data, supplier data, research, budgets and strategic plan.
Why?
To get a competitive advantage, using the competitor’s valuable data.
Who?
Defence, automobile, pharmaceuticals, electronics, software, retail, construction, engineering
International response
Interpol, the UK National Crime Agency (NCA) and the US Federal Bureau of Investigations (FBI) are just a few of the organisations who have created information and resources to help individuals and organisations combat the rising tide of computer based crime. In terms of risk the Institute of Risk Management (IRM) has produced a detailed handbook which provides in-depth analysis and insight. It explains the nature of the risks and provides practical tools and techniques to address them.
The IIA contributed to the handbook's production so our members can access it for free and in full using the link Cyber Risk - Resources for Practitioners as well as a much shorter executive summary.
Global IIA have published a paper on what board directors need to ask about cyber security. The report outlines the five principles that all corporate boards should consider 'as they seek to enhance their oversight of cyber risks', along with some questions the board should consider. Download the report.
Governments and regulators have also responded by introducing new rules supported by penalties for those who fail to comply. For example, the European Union’s (EU) rules on data protection and data transfer are among the most stringent and are set to get tougher under the General Data Protection Regulation, which is expected to come into effect late 2015 or 2016 across all 28 member states.
Varonis who specialise in ‘Big data’ issues, data protection, compliance and auditing have prepared a paper summarising the key detail of the regulations with seven tips to achieve compliance that internal auditors may want to bear in mind:
- Minimise data collection. The proposed EU law has strong requirements that companies limit the data they collect from consumers.
- Report promptly. Data breach notification is a new requirement that EU companies will have to address.
- Retain carefully. The new law’s minimisation rules apply not only to the scope of the data collected but also how long it is kept.
- Beware the new definition of personal identifier. The EU has expanded the definition of personal identifier, this change is important because the EU law centres on protecting these identifiers.
- Use clear language. The organisation will need explicit consent — an 'opt-in' from the consumer when collecting data.
- Find the delete key. “Right to erasure” means that when consumers withdraw consent on data they’ve given, companies will have to remove it.
- Cloud computing doesn't escape the new law. “When companies decide to process data in the cloud, they’ll have to get assurance that their provider has the required security measures in place.”
UK government national cyber security strategy
A primary objective of the UK government's national cyber security strategy is to make the UK a safer place to conduct business online. However, determining the benefits of cyber security and knowing where to start are a significant challenge for many organisations.
The Cyber Essentials scheme has been developed by government and industry to help organisations protect themselves against common cyber attacks. The Cyber Essentials Scheme summary provides a clear statement of the basic controls all organisations should implement to mitigate the risk from common internet based threats, within the context of the Essentials 10 steps to cyber security.
For managers and internal auditors there are additional guides that set out controls for basic cyber protection and through the assurance framework it offers a mechanism and certificate scheme for organisations to demonstrate to customers, investors, insurers and others that the organisation has taken essential precautions.
Cyber security should therefore be regarded as a business issue rather than a technology issue. Board members need to understand how cyber security risk affects business decisions and strategy.
Cyber security and internal audit
Cyber security presents a problem for internal auditors.
- The risks are constantly evolving so keeping up to date with what is happening is a real challenge.
- Every organisation is different so the organisation’s priorities around cyber security, while not unique, will have subtleties that internal audit needs to understand. This means scheduling time with internal experts to really appreciate the risks that impact the organisation as well as gaining an appreciation of assurance needs and expectations.
- Perhaps the greatest challenge is to consider in the light of the issues mentioned whether internal audit has the necessary expertise to provide assurance. This is most important given the International Standards (Standard 1210 Proficiency) say internal auditors must possess the knowledge, skills, and other competencies to provide assurance.
Acquiring and holding on to such expertise within internal audit can be difficult and costly, which is why many functions turn to co-sourced arrangements. This is a genuine option and one that many rely on as a consequence of the depth of assurance that is deemed necessary.
On the other hand internal audit should not shy away from the challenges and should approach cyber security in much the same way as other risks. Richard Chambers, president and CEO of the Global IIA, says the current cyber security threat is somewhat similar to the Y2K (millennium bug) concern that gripped companies at the end of the 1990s. 'It was a business process issue as much as it was an IT issue,' he says. 'In that regard, cyber security is not unlike a lot of business issues in terms of how internal audit would address it.'
The NIST Cybersecurity Framework, which was drafted by the US Commerce Department’s National Institute of Standards and Technology (NIST), comprises of a risk-based compilation of guidelines. These guidelines are able to help organisations to identify, implement, and improve cyber security practices. Based on the NIST framework, there are five core functions of effective cyber security, that are listed below along with definitions:
Identify
An understanding of how to manage cyber security risks to systems, assets, data and capability.
Protect
The controls and safeguards necessary to protect or deter cyber security threats.
Detect
Continuous monitoring to provide proactive and real-time alerts of cyber security related events.
Respond
Incident response activities.
Recover
Business continuity plans to maintain resilience and recover capabilities after a cyber breach.
From this perspective internal audit can ask a number of basic questions based on the above core functions:
Identify
- Does the organisation know what its most precious information and data is ('the crown jewels')? What is it and why is it important?
- Do employees know what is expected of them in terms of keeping data and information secure?
- Does the organisation have clear policy and procedures relating to cyber security?
- Are policies and procedures also communicated to and applied by the external partners the organisation depends upon?
- Is there clarity upon the ownership of the risks and controls?
Protect
- Where are the data and information kept, how is access controlled and who actually has access to the data and information?
- Have risks associated with loss and theft be identified and assessed?
- Does risk mitigation maintain risks within agreed tolerance levels?
- Are third parties verified/checked prior to being given access to sensitive areas?
- Have outsourcing and supply chain risks associated with data been properly identified and evaluated?
- Do employees receive guidance, training and specific instructions?
Detect
- Do managers monitor, test and report upon risk mitigation?
- Are incidents and their impact reported to senior managers and the board?
Respond
- Do incidents, internal and external, prompt reassessment of risks?
- What would happen in the event of security breach – is there a response plan? (see separate section on this subject)
- Have these procedures been fully applied when needed with lessons learnt and corrective action?
Recovery
- Is an IT disaster recovery plan put in place?
- Does the IT DR plan include key elements such as RTO (Recovery Time Objective), RPO (Recover Point Objective), Key IT systems universe, detailed recovery procedures, etc?
- How often is the IT DR plan being updated?
- Does the organisation have a Business Continuity Plan (BCP) plan?
Applying a risk based approach in this way can help to illuminate vulnerabilities or weak spots giving an initial view upon the adequacy or inadequacy of risk mitigation and controls.
IIA workshops and webinars on this subject have underlined that is best to focus on the overall process of how data and information is governed rather than the specific tools and techniques used. This is because tools and techniques usually address one specific risk, and they may do that quite well but they may also be useless for every other risk. If the overall process for governing information is weak tools and techniques won’t do much good.
The list of basic questions does two other things. It prompts a discussion of what managers (first line of defence) and what internal assurance providers (the second defence) do to detect and prevent cybercrime from occurring (without necessarily debating the three lines of defence model). In doing so it will highlight where best to acquire and apply external expertise, if any is needed, for example, the use and extent of penetration testing.
It is important that heads of internal audit have discussions with their audit committees, who may need a steer on what questions they should be asking of management. In particular they need to be aware that cyber security is not just an issue for IT managers, and that 'techies' may focus on the technical security issues while the immediate threats may be people-related and therefore need a more holistic approach.
Preventing internal data breaches
The roundtable meeting in May 2015 highlighted that a disgruntled employee can cause more damage than an external cyber attack as the perpetrator generally has more time to gather the data they want and have a better idea where to find it. The well publicised US National Security Agency (NSA) data breach of 2013 by Edward Snowden who worked as security contractor is probably the best example of what can happen when trusted insiders have widespread and uncontrolled access to the organisation’s data.
The reality is most organisations have no procedures in place to deal with insider threats. As organisations invest large sums of money into cyber security to prevent external attacks they assume those with internal access are trustworthy. But as the NSA case shows once an insider has the necessary access privileges the potential for damage increases significantly. As many organisations don’t monitor their internal network traffic, an attacker can take their time collecting data. Once all of the target information is packaged in a central location on the network, the attacker can then move it out of the network in one go.
In some cases internal users with no ill intent can inadvertently be responsible for a serious data breach. This occurs when data is released or attackers gain access to data through various forms of phishing.
Prevention and detection mechanisms are the key to tools to combat potential internal data breaches. One of the first things to look at is who has administrator access that gives permission to virtually all files and data, including confidential documents and emails. The obvious question to ask is – why do they need it? Furthermore practical measures need to be in place to alert IS managers of the following activities:
- Unauthorised access
- Violation of organisation policies
- Internal reconnaissance
- Data hoarding
- Data loss
These are all areas internal auditors can review. This should include providing assurance that effective controls have been installed arising from incidents and lessons learnt. Finally, there are two other issues for internal audit to consider. First where organisations hold and manage vast quantities of data it is worth looking at whether the organisation employs a data analytics tool to bring potential issues to the surface for investigation. Second, if and when, a data breach occurs is there an audit trail to identify what happened, when and where?
Proactive data analytics for investigation
In order to ensure that potential issues are brought to surface for investigation, the red flags in the data should be proactively identified through a data analytics methodology.
Based on the Association of Certified Fraud Examiners (ACFE), examples of the areas of red flags are listed below:
Areas of red flags
1. Corruption
Examples
- Is there conflict of interest between the staff and the customers/vendors/suppliers?
- Is there collusion to disadvantage the company between staff and the customers/vendors/suppliers?
- Is the company facing cash flow issues?
Example of possible data analytics
- Aging of the accounts receivables
Source of data for analytics
- Database of financial systems.
- Audit trail.
2. Asset misappropriation
Examples
- Are there any ghost vendors or ghost employees?
- Are there any vendor companies that have a relationship with existing employees?
- Are there any anomalies in the expense claims?
Examples of possible data analytics
- Matching of the employee names with the vendor names.
- Check whether there are duplicate claims for the expenses.
Source of data for analytics
- Database of financial systems.
- Audit trail.
3. Fraudulent statements
Examples
- Is the revenue recognition timing adhered correctly?
- Is sufficient segregation of duty policy put in place?
- Does management display a significant disregard for regulations or controls?
Example of possible data analytics
- Check on whether the operational financial transactions (e.g. posting of journal vouchers) are performed by management staff.
Source of data for analytics
- Database of financial systems.
- Audit trail.
To extract the data, the internal auditor can work together with the IT team. The diagram below shows the high-level steps to perform the data extraction and analysis:
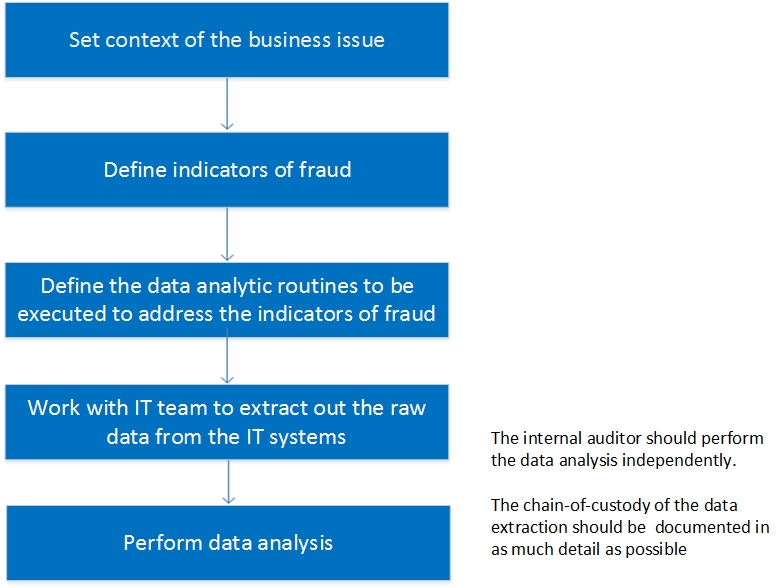
The chain of custody refers to the preservation of evidence from the time it is collected to the time it is presented in court. It is important to prove that the evidence has remained intact for the following purposes:
- That the evidence offered in court is the same evidence they collected or received.
- To the time and date the evidence was received or transferred to another provider.
- That there was no tampering with the item whilst it was in custody.
The data extraction should include screenshots on the timestamp from the audit logs. The screenshots can also show the number of records extracted from the source IT systems which concur with the number of records processed by the internal auditors.
Training and security awareness
Based on the Institute of Internal Auditors Research Foundation (IIARF) report on cyber security, it was mentioned that cyber security needs to be treated as an enterprise-wide risk management issue, not just an IT issue. Therefore, the board has to ensure that everyone in the organisation understands cyber security and not just delegate cyber security to the IT personnel.
Security awareness briefings should be conducted on a regular basis for all employees in the organisations. Good practices on end user security hygiene habits should be shared with all employees during the security awareness briefings.
The rigour of the organisation’s end user computing policy dictates the type of acceptable end user computing behaviours. Whenever end users are in doubt about a particular situation, the end user computing policy should be able to provide guidance to navigate around the situation. The end user computing policy also helps to cultivate a culture of computer ethics in the organisation. Computer ethics can be broadly defined as the ethical use of computer to prevent harm to everyone.
As the IT personnel are the front liners to respond to any cyber attack on the organisation, it is imperative that the IT staff are equipped with the latest technical knowledge to carry their duties effectively. The different areas of technical knowledge are in the areas of security operations, security engineering and technology. The organisations can send their IT staff for formal academic studies or seminars.
Cyber insurance policy
The board and senior management also need to initiate discussion to avoid, accept, mitigate, or transfer cyber risks through insurance. The previous sections have provided details on the way to avoid, accept or mitigate the cyber risks.
Cyber insurance policies are one product developed to cater to the transfer of risk arising from cyber activities. Information security professionals have an important role in identifying cyber exposure, putting in place preventive techniques and determining the security gaps. The adoption of cyber insurance will become an increasing important topic in cyber security.
There are many drivers for the growth of the cyber insurance industry. One of the key drivers is that cyber insurance is being positioned as a way to handle the residual risks. This is because preventive, detective and corrective controls implemented by an organisation cannot completely eliminate cyber incidents. Governments and various industry regulators have also intensified pressure on businesses to protect personal data, using significant fines for any breaches.
There are two main cyber insurance policies, namely first-party risk exposures and third-party risk exposures. First-party coverage insures against damage to and costs incurred directly (except regulatory fines) by the insured organisation. Third-party coverage insures against liability, damages, expenses incurred in responding to allegations against an insured company made by third parties arising from cyber attacks and cyber breaches.
Further reading
BIS Cyber risk management - a board level responsibility
HM Govt. FTSE350 Cyber goverance health check tracker report
HM Govt. Principles of effective security risk management
ICSA Guidance note - cyber risk
European Commission: Data protection reform
Take control of your personal data