Heads of Internal Audit Virtual Forum
2 September 2020
Please note:
- All Institute responses are boxed and highlighted blue.
- Where the chair comments in that capacity, this box is highlighted in yellow.
- For confidentiality, the identities of all delegates/attendees are anonymised.
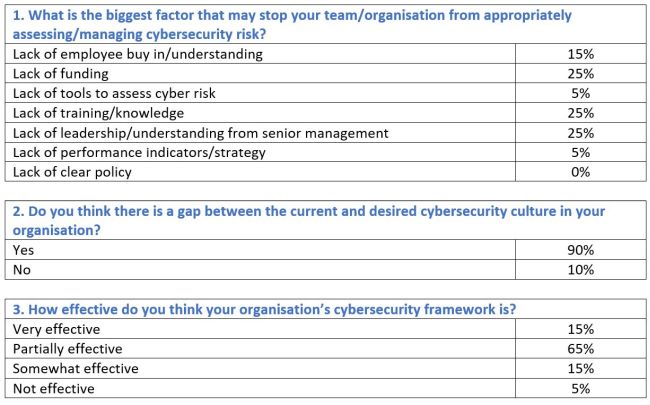
Chair’s commentsCyber security has been recognised as one of our key risks for a number of years now and will feature once again when we publish our Risk in Focus 2021 report on 22 September 2020. It was certainly one of the primary topics when we selected the priorities for the forum a few weeks ago. Potentially because many of you see it as a high inherent risk and, given the constantly and rapidly changing environment, a high residual risk as well. It is also a subject which we sometimes find difficult to deliver sufficient assurance over. Occasionally due to availability of skills or resources to buy them in and sometimes due to the multitude of other priorities we have. Today’s speaker is Noel Comerford, Senior Manager, Cyber Risk Services in Deloitte. Noel will provide, what I hope for many, is confirmation of your current approach to the subject and for some, a challenge to your current approach. The talk track supporting today’s session will be shared on our web page along with responses to the questions raised. At the start of the Forum we ran a quick poll, the results of which are shared below. |
The talk track slides supporting today’s session along with responses to the questions raised can be accessed below:
Reflections/Key takeaways
Our reflections from the session are noted below.
- Break it down – Cyber is very broad and diverse, and difficult for people to get their head around and absorb. Cyber needs to be broken down into bite size pieces and put into context for your organisation.
- Employees and third parties seen as a weak spot – Whilst these sit within the ‘trusted circle’, we tend not to have as much control here and the perimeter has expanded with COVID-19 and remote working.
- Resilience around employees – Eg disgruntled employees and accidents by employees. Not all cyber incidents are caused by maliciousness, sometimes it is caused by human error. There is a lot of scope here for looking at how resilient organisations are.
- Support the mindset - Internal audit can support the mindset around cyber where the scope is not clear. Initially internal audit should take a more advisory assurance approach. How do we assess a security function? What benchmark are we going to use? What Standard are we going to use? What kind of metrics? What does good look like?
- Focus on the mindset - Look at how the organisation runs security. How is it organised? Who is in charge? Is it at an appropriate level?
- Tailoring cyber to the organisations business context – Its funding and its capabilities. If, for example, you choose to audit the cyber programme against Standard ISO 27001 but you’re not near that level of capability, then it will have a very poor or contentious result. If you audit to that level without understanding your threats and your risks, are you really driving any value into understanding, or understanding where remedial actions is necessary?
- You can’t protect everything - You can’t apply the same level of controls across your entire ecosystem at an economic and feasible level.
- The right team - Should we assess our cyber skills capability? Do we have the right team in place with the right attitude? Is the right training programme in place?
- Governance – Look at governance arrangements without purely looking at the cyber security function. What controls are in place? How have the controls been chosen? Why are they in place? What are they designed to protect? Are we protecting against the right threats? What does our risk model look like? How do we assess what cyber threats are relevant and are those controls relevant for that threat? If they are relevant for that threat, how do we understand whether the control is operating effectively?
- Extending the area of governance to effectively monitor cyber security - How well is cyber understood and managed in the business? Look at cyber as digital health and safety – where there is a risk to human life or accidents in the workforce it tends to be taken seriously and it tends to be run from the top and it is everyone’s responsibility.
- Business areas – How well do they understand cyber? How well are they engaged with the cyber programme? How understanding are they of cyber tools and cyber controls?
- Compliance with policies – You are carrying a higher risk of exposure for being non-compliant with your own policy than just having a bad policy. It is a lesser audit finding to say your policy is weak you need to include more in it, as opposed to, you’ve actually got a policy, but no one follows it.
- Peer review – This is an area that provides no real indication as to how you are managing risk. If another organisation in the same sector is doing cyber badly, it does not provide you with any degree of assurance or confidence that you are managing the risk to your own organisation. Continually engage and challenge and look across the organisation, drive conversations: So, what are we trying to achieve? What is our objective here? Why do we have the objective?
- Challenge the level of understanding from within the organisation – This can be done very effectively without going anywhere near the cyber function at all. If you can get to the stage where you have the confidence that the business understands that there is a cyber risk, and they understand what the cyber risks are, and the cyber security/IT team have documented the controls against those risks and threats, you are in a good place.
- Value of the costs of the controls versus the cost of exposure – this needs to be balanced eg running a phishing campaign to test staff resilience to clicking on fake links in emails – what is the level of exposure? If there is a reduction in staff clicking on emails, offset against the harm done to the business it is likely to reduce business losses over time.
- Look at outcomes not causes – if the cyber team perform a review as to what the risk models look like and map it out as an ecosystem in its own right, you can focus in on your critical systems and put protection plans in place where they are needed most.
- Metrics – these can be a challenge; raw cyber metrics might be used to help inform management information, but maybe should not be delivered directly and cannot be trusted out of context. For example, if 85% of all systems are patched within a month it doesn’t really support a risk decision if it turns out that all key systems are within the 15% that are not patched.
Institute's commentsThe key message coming out of this is that, as internal audit, we need to be very mindful of providing false assurance. Tackling a topic that we are perhaps, not competent to tackle presents a risk to the organisation. Whilst not suggesting that we use competency as a wall to hide behind if we think a topic is too difficult for us, I do think that we have to be mindful of the ability to undertake a piece of work in this space, looking at it from risk and internal controls. The speaker talked about governance structures and where cyber sit within your organisation.
The impact on the organisation of a cyber-attack can be catastrophic. We saw it with the NHS a few of years ago when they had an attack. Transfer that attack to now, or earlier this year when the NHS was tackling COVID-19, something like that would have been horrendous. We have a duty to be mindful of all of this across our organisations. No surprise, it is the number one risk in our Risk in Focus 2021 report. As internal auditors, we have an obligation to our organisations to flag our concerns. There is also an obligation on us to be honest, if we don’t have the skill set in our team to undertake audit work in this space, then we flag it to the audit committee and obtain the necessary support. The biggest concern is false assurance. Added post the meeting Internal audit can offer its view on the extent to which any relaxing or adaptation of controls has increased the risk of data leakage or security breaches. The real question is - what has changed? That applies externally (eg a rise in phishing attempts) and internally (eg lack of staff cyber awareness training post crisis or security patching of homeworking devices not being managed as effectively as on-site). By understanding where the most disruption lies as well as where the highest-value data assets reside, internal audit can determine the impact of any change on the organisation’s information security risk and the control environment that is in place to mitigate it. Staff awareness and understanding of information security risk is absolutely essential. This applies to protocols around the use, management and storing of confidential data to prevent data leakage, and applies to ensuring workers know how to spot cybercrime to avoid people succumbing to phishing and spear phishing (targeted at a specific individual) attempts which can result in costly malware and ransomware attacks and fraud by deception. Internal audit can and should check whether cybersecurity awareness is being sufficiently fostered and whether staff training has been updated in light of changes to the working environment and IT infrastructure. It should also attempt to provide assurance that staff are not circumventing processes to save time and effort. Internal audit can also be a sounding board for information security teams that may be forced to adapt the IT control environment to keep the business operational and as efficient and productive as possible in the face of shock events. Any high-risk control changes will need to be reported to senior management to check that they are within the organisation’s cyber-risk appetite. Finally, the survey you completed at the start of the session today identified that 90% of you believe that there is a gap between the desired and current cyber security culture in your organisation. As a headline, this is a very significant comment and certainly appears to suggest that there is still a lot that we can add in terms of guidance to our organisations. |
Chair’s commentsOur next meeting will be on the 16 September and will focus on culture. If you can have a look at the agenda and if there are any other topics you would like to include and/or if you would like to contribute; we are keen for Heads of Audit to present on each of the topics we are covering in these sessions, please contact me at derek.jamieson@iia.org.uk A topic that I have been discussing today is Diversity and Inclusion, and whether internal audit should be providing assurance on this subject. It has a regulator focus now; I don’t know how many of you provide assurance around this and would be interested to hear from anyone interesting in talking about this in a future session. If you have any thoughts you would like to share, I would be interested in having a conversation with you to position this topic for the future. Following the previous session on data analytics, we will be creating a discussion group; further information will be provided in due course. |