Local Authority Internal Audit Virtual Forum
24 March 2021
Please note:
- All Institute responses are boxed and highlighted blue
- Where the Chair comments in that capacity, the box is highlighted in yellow
- For confidentiality, the identities of all delegates/attendees are anonymised
CEO welcomeOver the last decade, cyber-attacks have become one of the biggest security threats to governments around the world, including the UK and Ireland. As the world becomes more interconnected, digitised and open, this threat is likely to only increase. Threats can have various origins like state-sponsored attacks or terrorism. Attacks are also wide-ranging, from sophisticated operations on critical national infrastructure, to individual level attacks aimed at getting access to a high-volume of personal data (the latter rising in prevalence in recent years). During the COVID-19 pandemic, the surge in home working – including in the public sector – has increased vulnerabilities. According to a recent report from INTERPOL, this shift has occurred concurrently with an uptick in cyber criminals targeting governments and critical health infrastructure, as opposed to individuals and small businesses. It will be interesting to hear what our speakers have to say. Our speakers today are Katie Owen, Cybersecurity Advisor, and Owen Pritchard, Cybersecurity Programme Manager, who both hail from the Local Government Association. We are also joined by Liz Sandwith, the Institute’s Chief Professional Practices Advisor and Derek Jamieson, Regional Director. |
Key takeaways
The Chartered Institute published its cyber security report, Mind the Gap: Cyber security risk in the new normal last month.
Over half of the respondents to the report (51%) admitted to having suffered a cyber-attack in the previous twelve months.
Competing priorities were noted as the main barrier to implementing good practices during the pandemic, followed by employees working remotely and insufficient budgets.
A strong cyber security culture has never been more important. However, it is only a minority of CAEs who contribute to cyber security strategy and policies, assess cyber security training and discuss cyber security risk with the board.
The report highlights three key actions for internal auditors.
- Internal audit is best placed within the organisation to access and ensure that cyber security risk is widely understood by all employees, which would mitigate the likelihood of policies and procedures being circumvented during times of increased stress and competing priorities.
- Internal audit must have a thorough understanding of what influences cyber security culture and be able to share this with management and the board in order to influence the organisation's cyber resilience.
- Internal audit has a role to play in promoting cyber security awareness across the organisation and providing assurance that a robust cyber security awareness culture has been established and is operating effectively.
Click here to read our new cyber security report in full.
Presentation: Katie Owen - Cybersecurity Advisor, Local Government Association
- Cyber threats become a successful cyber-attack when defences are breached due to a vulnerability leading to an incident.
- Cyber risk is a function of vulnerability and threat.
- Vulnerability is about protection and preparedness
- Threat is about intent and capability
- There is no such thing as 100% cyber secure so we need to prepare to reduce impacts.
- Protection and preparedness are within our gift to alter.
- In a June 2020 National Cyber Security Centre (NCSC) report, it was highlighted that ransomware attacks are the greatest threat to LAs, and that the rise of home working due to the pandemic increases vulnerabilities.
- People, processes and technology all need to work together to promote sustainable cultural change and to deliver a cyber culture.
- NCSC's Cyber Assessment Framework has four pillars which provide useful guidance
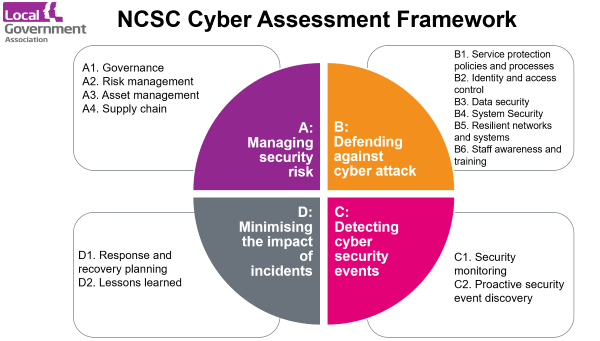
- (A) Managing cyber security risk requires
- Governance – structures, policies, processes
- Risk management – identification, assessment and understanding
- Asset management – understanding and dependencies
- Supply chain – confidence in security of suppliers
- (B) Defending against cyber attack
- Tools such as service protection polices and processes, identity and access control, data security, system security, resilient networks and systems, staff awareness and training.
- (C) Detecting cyber security events
- Security monitoring and proactive discovery of malicious activity
- (D) Minimising the impact of incidents
- Response and recovery planning – well defined and tested
- Lessons learnt – understanding root cause for remediation
- A blend of leadership, governance and awareness is essential to embedding a cyber culture and to ensuring that a range of measures are in place. These measures include accountabilities, policies and processes, scrutiny and training.
Cyber security is an issue for the whole workforce not just IT.
Click here for the presentation slides.
Useful resources from presentation
Please see below a list of all the useful resources highlighted during the presentation:
NCSC |CAF framework – Cyber Assessment Framework
NCSC | Active Cyber Defence Tools these are free for councils; please raise awareness.
NCSC |10 Steps to Cyber Security
NCSC |Incident Management information and 3-2-1 back up guidance
NCSC | Cyber Essentials
National Audit Office | Cyber security and information risk guidance for Audit Committees
Reform thinktank report | Resilient public services in an age of cyber threats
Institute's commentsIf you are a HIA, CAE or Principal Internal Auditor, please complete our Risk in Focus 2022 survey before 12 April. Thank you. Click here for the survey. Our next LA Forum meeting is on 21 April 2021 and addresses ESG (Environment, Social and Governance matters). The reality is that much of what organisations are doing now to meet ESG expectations is equally relevant in local authorities, the public sector and other sectors. Our speaker will outline ESG, including some of the key expectations that come with it, and provide us with a view of the need for assurance from internal audit. Please contact Liz Sandwith liz.sandwith@iia.org.uk if you have any practical experience that you are willing to share during our ESG forum such as climate risk, culture, governance, environmental or social agendas. And, as always if you have any ideas or suggestions for what we might include in future agendas please also contact Liz. |
Q&A and chat box comments
Q Were you surprised at the number of cyber-attacks that respondents reported in the Institute’s Mind the Gap research report?
A No - there are a range of incidents being identified on a daily basis. It’s all the more reason to be prepared for the eventuality that one will happen.
Q Does the LGA website have a dedicated section on cyber security?
A No - not a huge amount of information. Please use the email addresses at the end of the slide pack if you would like to get in touch for support. The strategy is to push information about policy and standards rather than act as a professional body. One project we might explore is preparing questions for specific roles such as internal audit or audit committees to ask about cyber risk.
Q Do you believe that senior management fully understand the potential implications of a major incident and their potential accountability.
A Unfortunately not. It needs to be improved and it’s a key part of our role. Awareness and understanding priorities is important and desktop exercises are invaluable. The last decade is the first time since WW2 that LAs have come under direct threat. Most LA leaders are not digital natives, so it’s often not understood at the highest level. Understanding that cyber risk is an intersection of people, process and technology is a journey.
Q What role does internal audit have in helping leaders with their cyber journey.
A To be honest, I thought the three actions at the start of this session were a pretty strong strata. No-one expects internal audit to be technical experts. Internal audit needs to be at a strategic level, so the NSCS CAF works well. Understanding it and asking the questions, you don’t have to answer them yourselves, just know that the answers are wrong. This is the skill of internal audit: knowing the questions to ask, to dig. Use the CAF framework as a guide for the questions to ask.
Q You spoke earlier about minimising impact of incidents – how have you seen this working in practice?
A Where incidents have been dealt with effectively, LAs have had tested plans in place. Doing the thinking in advance really pays benefit. A robust approach to back-ups enables organisations to continue. Being able to maintain communications is really important, not relying on electronic systems but having options.
Q We’re conducting our first IT/cyber security audit this year. Would you recommend outsourcing given our lack of experience?
A Not necessarily, using the CAF pillars is an important starting point. The NCSC have certified suppliers to help with sourcing service providers.
Comments
- We completed an audit of Cyber in 2019. Looked at the Council against the September 2017 publication by the National Audit Office, ‘Cyber security and information risk guidance for Audit Committees’
- Our external IT support firm is currently an audit in this area for us
- Cyber essentials is a great start to look at their self-assessment tools to build a TOR from
- It can also be useful to use your insurance brokers to evaluate your arrangements. They should do this free of charge even if you don't cyber cover.
Contact details for our speakers - cybersecurity@local.gov.uk








